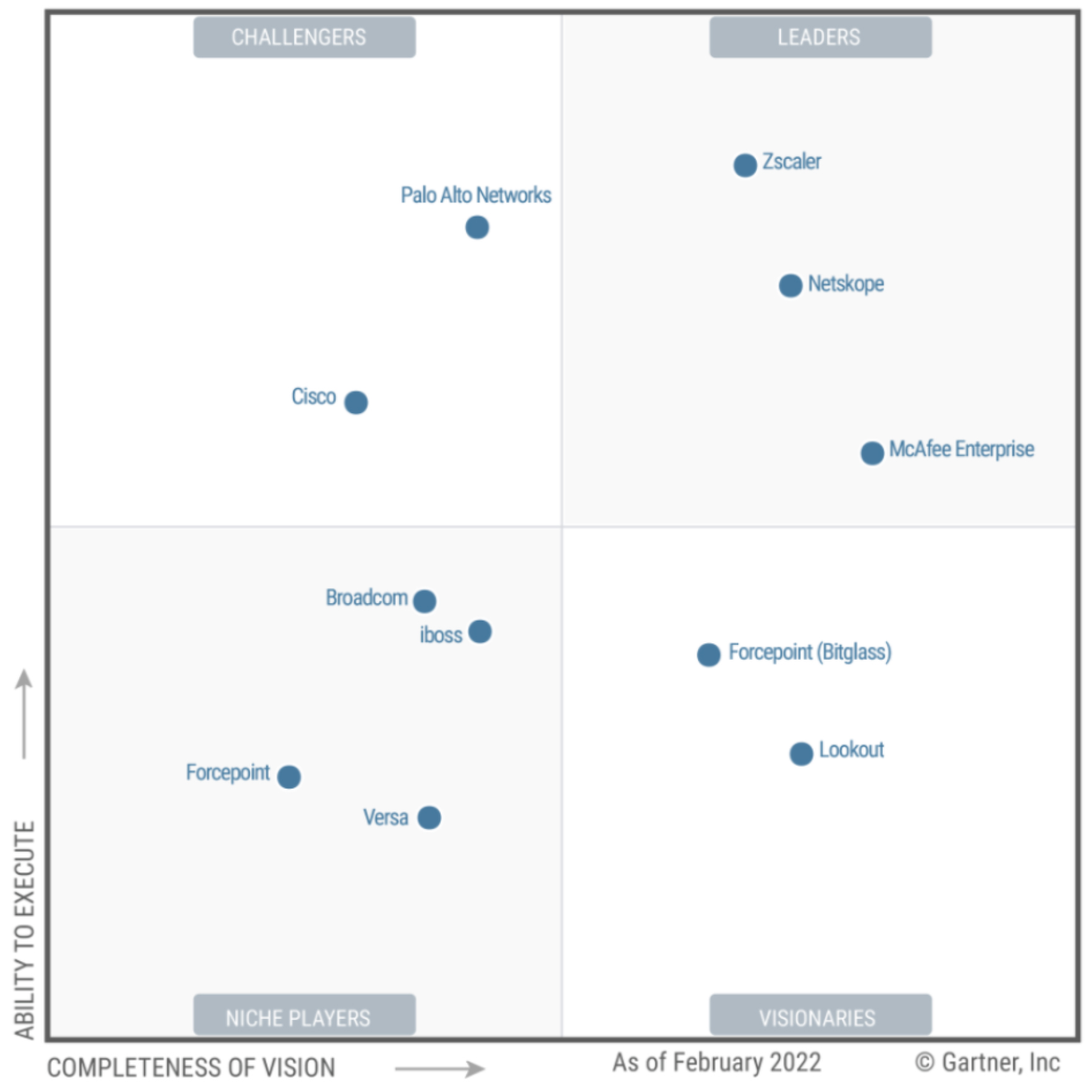
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Gartner Web Application Firewall 2023 . A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
A Waf Combines Positive Security Models, Signatures, Heuristics And Anomaly.
Gartner web application firewall 2023 . Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Gartner Web Application Firewall 2023
Gartner Magic Quadrant for Enterprise Network Firewall (20102022
Source: blog.51sec.org
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Gartner Magic Quadrant 2025 Firewall Test Annie Warner
Source: warnerannie.pages.dev
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Gartner Magic Quadrant For Network Firewalls
Source: mavink.com
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Gartner Magic Quadrant for Web Application Firewalls DETECTX
Source: www.detectx.com.au
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
[PDF] Magic Quadrant for Web Application Firewalls Semantic Scholar
Source: www.semanticscholar.org
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Gartner Magic Quadrant 2023
Source: www.decideom.fr
A waf combines positive security models, signatures, heuristics and anomaly. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
is a Leader in the 2020 Gartner Magic Quadrant for Network
Source: www.sworth.com
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Gartner Released Magic Quadrant For Web Application Firewalls Imperva
Source: www.tpsearchtool.com
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
A waf combines positive security models, signatures, heuristics and anomaly. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Gartner Magic Quadrant for Network Firewalls Results Ventas de Seguridad
Source: www.ventasdeseguridad.com
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Sse Gartner Magic Quadrant 2025 Sam C. Gottshall
Source: samgottshallc.pages.dev
Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Gartner Magic Quadrant For Web Application Firewalls vrogue.co
Source: www.vrogue.co
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Firewall Gartner Magic Quadrant 2023
Source: ita.animalia-life.club
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.
Gartner Magic Quadrant 2025 Firewall Test Annie Warner
Source: warnerannie.pages.dev
A waf combines positive security models, signatures, heuristics and anomaly. Wafs are deployed to protect web applications against external and internal attacks, monit or and verify access to web applications, and. A waf combines positive security models, signatures, heuristics and anomaly.